
Sepio Overview
Unmatched Hardware Visibility and Asset Risk Management
Sepio is a market-leading
Asset Risk Management (ARM) platform designed to reveal and control every physical device connected to your network—across IT, OT, and IoT environments. Its unique
Asset DNA fingerprinting operates at the physical layer, identifying devices by their electrical characteristics rather than relying on software signatures or behavioural patterns
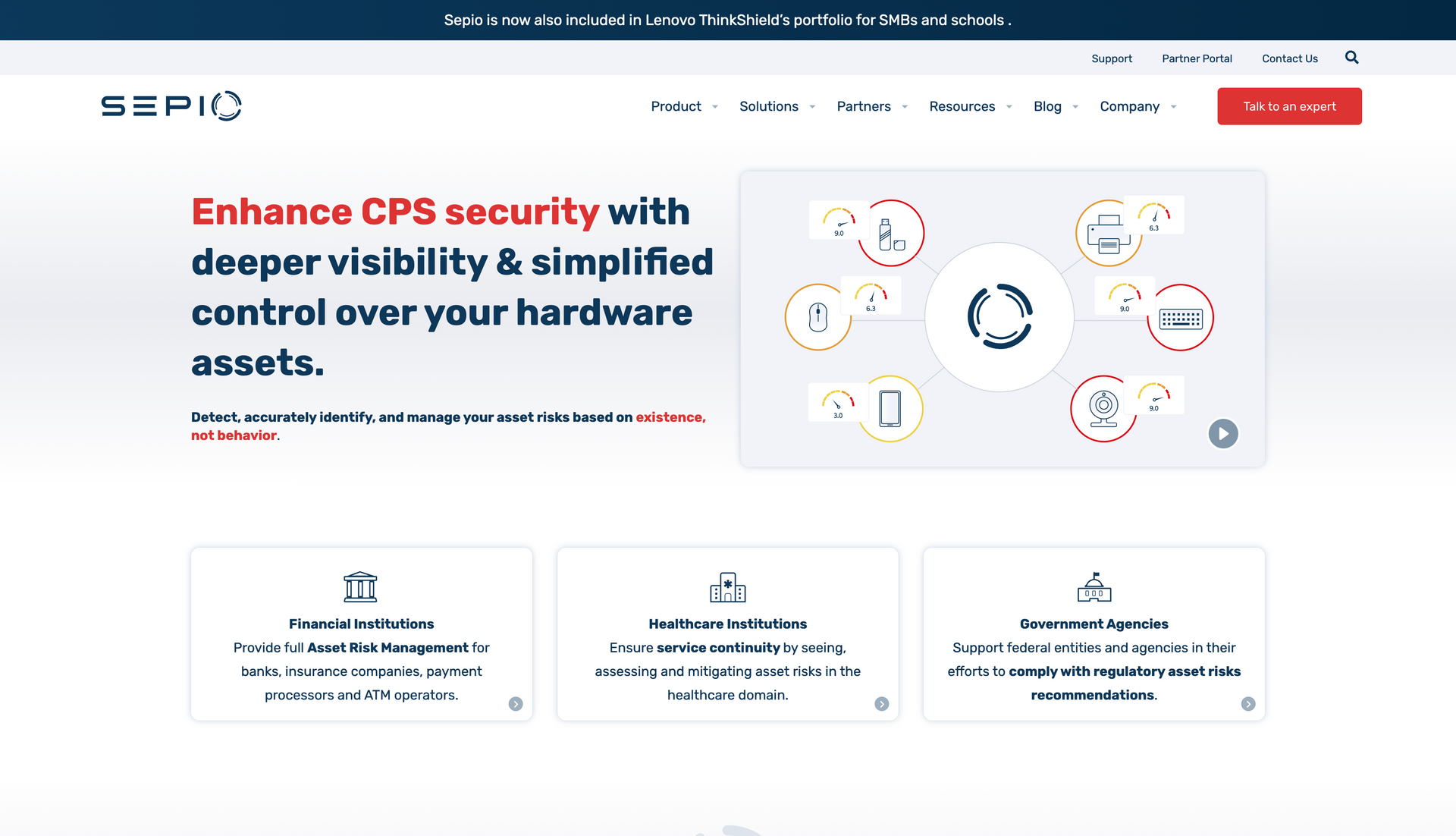
Core Strengths of Sepio
Complete Asset Discovery
Sepio passively monitors the physical layer to detect all devices—managed, unmanaged, shadow, or rogue—including peripherals and implants invisible to traditional
Dynamic Risk Scoring (ARF)
Using Asset DNA, contextual data (business function, location), and threat intelligence, Sepio calculates an Asset Risk Factor that prioritises devices for investigation
Fine-Grained Policy Enforcement
Administrators define policies based on device attributes—type, location, department—and Sepio automatically blocks or quarantines any device that violates them
Automated, Scalable Control
Sepio enforces hardware policies at scale with zero maintenance overhead, integrating seamlessly with NAC, SIEM, SOAR, or XDR systems to ensure swift responses
Intelligent Vulnerability Insight
Integrated OSINT and machine learning feed vulnerability intelligence into asset profiles—allowing teams to quickly identify and prioritise high-risk hardware
How It Works – Agentless, Agent-Free, and Trafficless
Sepio installs passively—requiring no endpoint agents or traffic inspection. It monitors signals at the physical layer
1.
Detects it instantly
2.
Maps its risk level
3.
Applies policies
(allow, block, alert)
4.
Logs events for audits and responses


Why Sepio Matters for Security Teams
Eliminates Hardware Blind Spots – Detects implants, spoofed devices, and unmanaged hardware in real time.
Tightens Zero-Trust at the Physical Layer – Ensures that only trusted devices are allowed into sensitive segments.
Boosts Compliance Posture – Supports CIS, NIST, GDPR, CISA, and other mandates with clear audit trails.
Integrates Seamlessly – Works alongside your existing security stack to fill gaps—without disruption.
Sepio has been adopted by global organisations in finance, healthcare, infrastructure, manufacturing, and government. It has received accolades from industry analysts (e.g., Gartner, Frost & Sullivan) for closing the critical hardware visibility gap that most cybersecurity tools miss.
Sepio Components
These modules can work together or independently—enabling flexible deployment tailored to your environment.
Endpoint Device Security
Scans USB devices with or without a light agent, evaluating plug-and-play hardware risk.
Network Device Security
Uses network taps or SPAN ports to discover all networked hardware—even those without IP or MAC addressesSepio+2Sepio+2Sepio+2Sepio.
Deploying Sepio with Zerium
Tailored architecture – SaaS or on-prem, fitting your environment
Policy design – Based on your unique operational risk and compliance needs
Integration – With NAC, SIEM, SOAR, XDR, and identity platforms
Training & enablement – For your IT and SOC teams
Ongoing advisory – To adapt as threats and regulations evolve



